Table of Contents
Why Port-Forwarding?
The main benefit of port forwarding is that the tunneled traffic between the user's computer
and the remote server is encrypted through the ssh protocol.
This allows secure/encrypted connections when using an inherently unencrypted protocol (like
FTP or telnet) between the user and the server's network. E.g. if a legacy system on the remote
network only offers unencrypted FTP, the user can create a ssh connection with port forwarding
between his computer and the remote network. The user will then use his FTP client to connect to the
local side of the tunnel and the ssh-client will encrypt the traffic and pass it on to the server
on the remote network where it is decrypted and forwarded the the FTP server. Thus the data will
be encrypted while traveling through the open internet.
Types of Port-Forwarding
The SSH protocol V2 offers three types of port forwarding:
- Local-to-Remote forwarding: Local (user side) port is created and all traffic
is forwarded to a predefined destination server and port.
- Remote-toLocal forwarding: A remote (server side) port is created and traffic
from connections to that port are routed to the local (user) computer and
is forwarded to a destination and port from there.
- Dynamic port forwarding: A local (user side) port is created and all traffic
is forwarded to a destination server and port. The server and port can be
chosen at connection time (this way the user's client/server combination
functions as a SOCKS-proxy).
Static Port-Forwarding
Static port-forwarding (or tunneling) refers to situations where the desitination
host and port are known in advance.
Programs and protocols which do not use data encrpytion (e.g. ftp or rsh) can
connect to the tunnel's port on the client computer and the ssh client will transmit
their data through the encrypted ssh connection to/from a final destination that is already
known at the time when the ssh-connection is made.
For example, a user can set up a port-forwarding on the client software, listening on the
client port 5514 and forwarding traffic to the address of an older device with a fixed IP address
on the remote network that only supports the unencrypted rsh protocol.
The user can then use a non-encrypting rsh client, connect it to localhost port 5514 and thus
will get connected via the secure shell client to the rsh server on the remote network. A normal
rsh client will not encrypt its data, but the ssh client will encrypt all traffic before sending
it through the ssh tunnel to the host on the other side
(and vice versa), essentially creating an encrypted rsh connection.
Dynamic Port-Forwarding
As outlined above, static port-forwarding feature requires the client to set up the tunnel
source port and destination before making the connection.
This problem is addressed by secure shell's dynamic port forwarding. With dynamic port forwarding,
the client sets up a listening port (as with normal port fowarding), but when a software connects
to the port, it can tell the client which host and port it wants to connect to. This is done
in the same way that client software can request connections from SOCKS proxies.
The ssh client will then forward the connection request to the secure shell server which makes
the connection to the destination host. This way, the ssh client could let an unencrypted ftp
software access ftp servers on the remote network through an encrypted data channel.
Connecting to an SSH-Server with Port Forwarding via ZOC
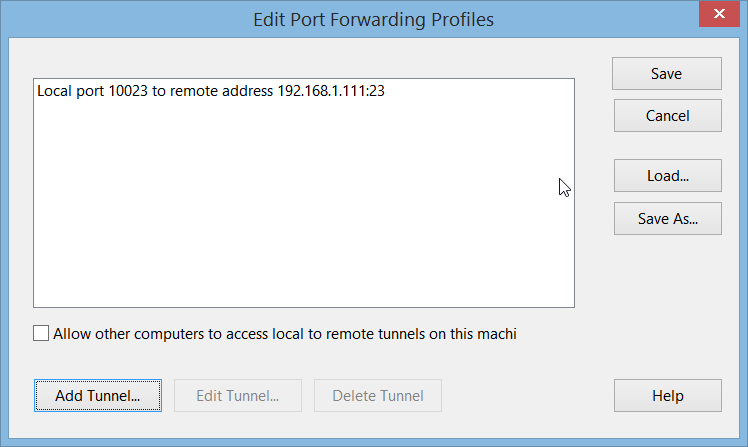
Assuming you want to create a tunnel from local port 10023 to a telnet server with IP
192.168.1.111 (port 23) on the remote network to create an encrypted connection to an
(otherwise unencrypted) telnet server.
In ZOC, this is done using so called tunnel profiles. A tunnel profile is a set of
predefined port forwardings (local, remote and dynmaic), that can be assigned to any
SSH session.
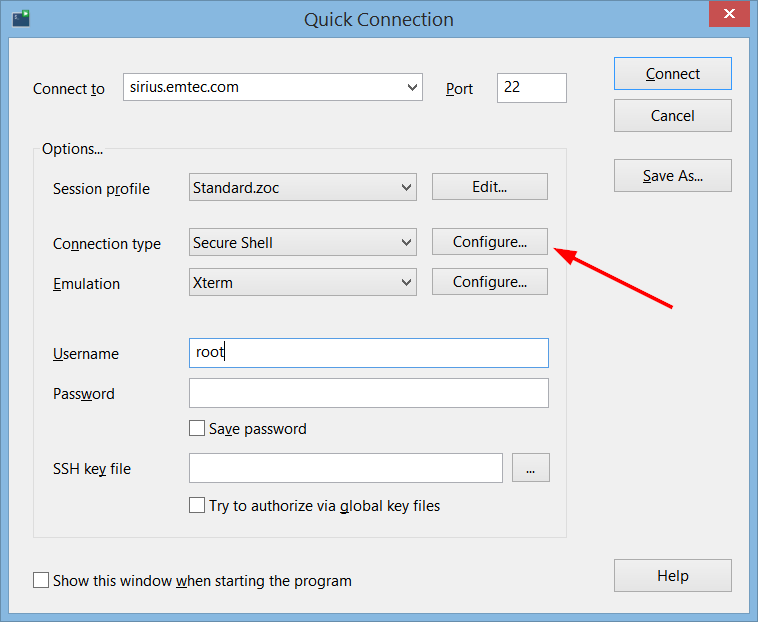
To do this, click 'Configure' where you select Secure Shell as your connection method
(e.g. in the host-directory or in the quick-connect dialog),
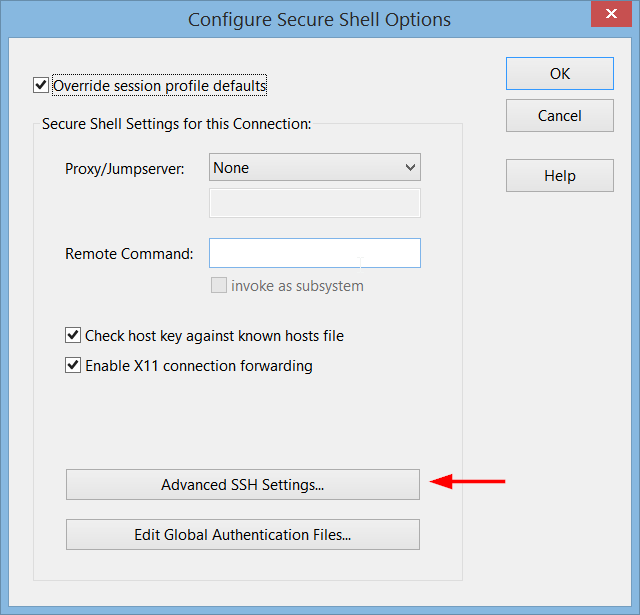
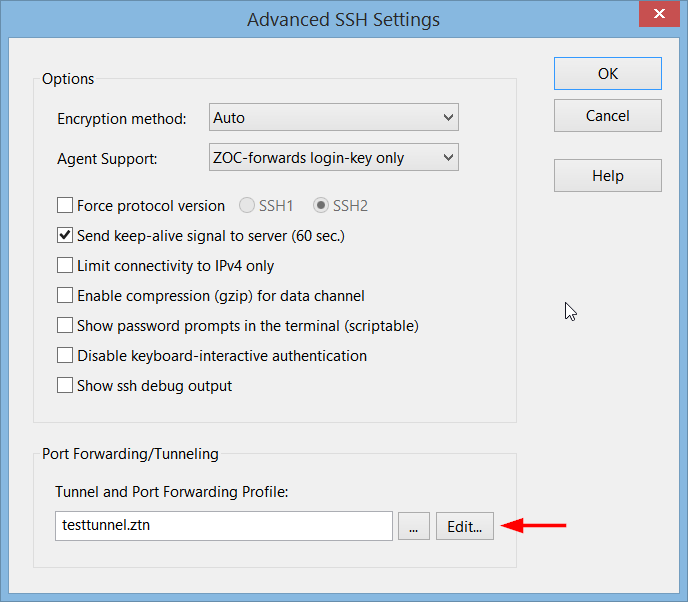
then click 'Advanced', enter a name for the tunnel profile and click 'Edit. There
click 'Add Tunnel' to create a local forwarding:
Connecting to an SSH-Server with Port Forwarding via OpenSSH
When using the OpenSSH ssh command on Linux, the -L <lport>:<rhost>:<rport>
option can be used to specify a local port and the remote server/port when making a connection, e.g.
ssh -L 10023:192.168.1.111:23 joedoes@myserver.somewhere.com
This will create a tunnel from the user's computer to the a telnet server that is only reachable
from within the remote network. The user can then use the
telnet localhost 10023
to connect
to the local side of the tunnel but will actually get an encrypted connection into the remote
network, reaching the telnet server there.